When you purchase through links on our site, we may earn an affiliate commission.Heres how it works.
The researchers say CoffeeLoader originated around September 2024 and has several similarities to theSmokeLoadermalware.
Once the malware has infected a system, it delivers several infostealers among them the well knownRhadamanthys Infostealer.

From there, it uses a number of tricks to stay undetected by antivirus programs and other security tools.
For example, it will run code on the infected systems GPU instead of on the computers CPU.
Since most security programs and antivirus scanners dont check the GPU, the malware stays hidden.
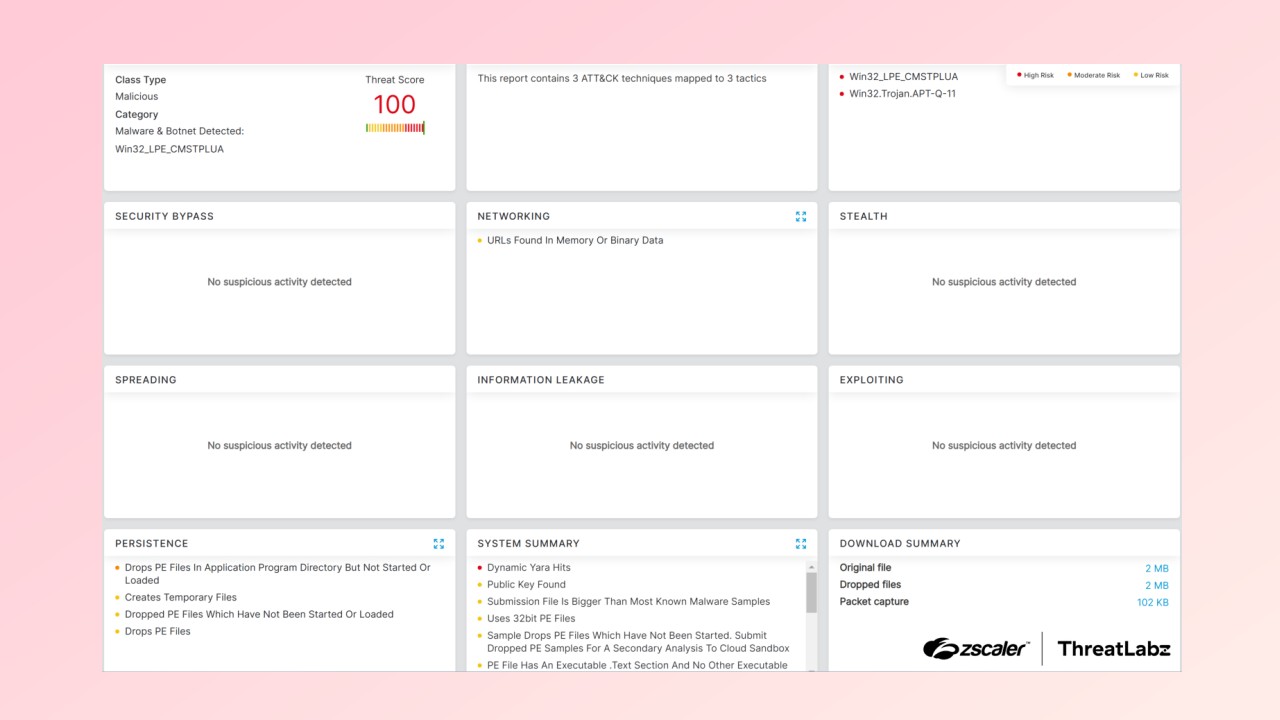
Another way it covers its tracks is by using a technique called Call Stack Spoofing.
This keeps it from being recognized as suspicious or harmful by any security software or antivirus programs.
It can also play dead or use a technique called Sleep Obfuscation.

The CoffeeLoader malware also accesses unusual pathways, for example, Windows Fibers, for evade detection.
The CoffeeLoader can then use these fibers to evade detection since security tools may not monitor them.
Hackers oftenimpersonate popular brandsand their software as a means to infect unsuspecting users with malware.