When you purchase through links on our site, we may earn an affiliate commission.Heres how it works.
The holiday season is a time for sharing, be it presents, food, or arguments.
Many of us travel to visit friends and family, and enjoy posting records of this on social media.

Image: How to edit photo metadata on iPhone
Before posting anything on social media, you should consider who can see it.
Reducing the amount of information about you visible on your social media account is another recommended action.
Avoid posting where you work and live, and where and when you were born or went to school.

Image: How to edit photo metadata on iPhone
Firstly, you should avoid publicly posting your travel plans.
Protecting your photo metadata may sound confusing, but it is actually simpler than you think.
An example of metadata is the date and time the media was taken, as well as the location.
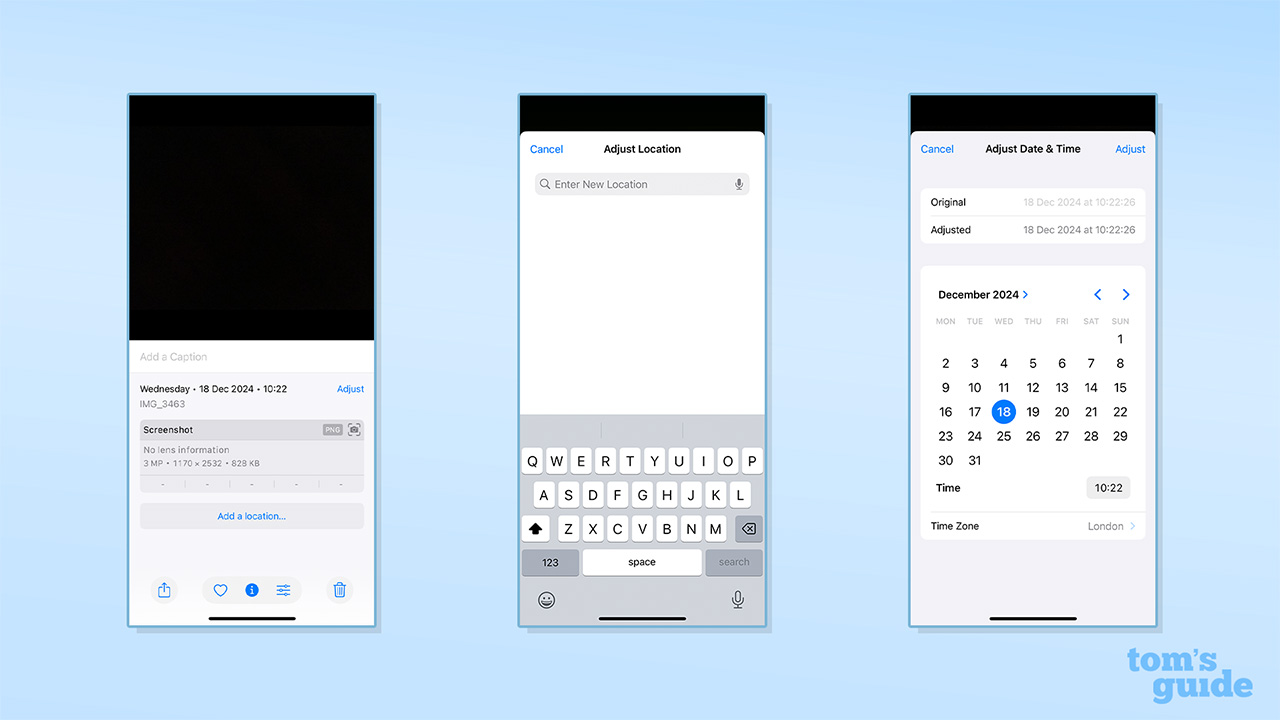
Image: How to edit photo metadata on iPhone
So turning off location prefs and disabling location tagging when taking photos or filming is a good tip.
If you are sharing online, then apps are also available to remove the metadata.
You should also respect your family or friend’s privacy and be wary of background details.

These can be an incentive for criminals, and could put you at risk.
“For instance, audio recordings could be analyzed to mimic speech patterns, tone, and mannerisms.
In such situations, it becomes incredibly difficult not to believe what you see and hear.”

Its important to stay mindful of how your shared content may be repurposed or accessed in the future.
Fake shopsare another popular scamming tactic used by cybercriminals.
They replicate the sites of popular online retailers and trick you into entering your personal information.

you’re able to best protect yourself from online scams by purchasing some of thebest antivirus software.
Other providers, includingIPVanish, andExpressVPN, offer a form of threat protection.
ExpressVPN also offers an identity protection feature known asIdentity Defender.

We test and review VPN services in the context of legal recreational uses.
For example: 1.
Accessing a service from another country (subject to the terms and conditions of that service).

Protecting your online security and strengthening your online privacy when abroad.
We do not support or condone the illegal or malicious use of VPN services.
Consuming pirated content that is paid-for is neither endorsed nor approved by Future Publishing.