When you purchase through links on our site, we may earn an affiliate commission.Heres how it works.
Another experiment let them recreate the path of a persons flight by tracking a games console.
Proximity wasnt a factor either, with hackers able to do all this from thousands of miles away.
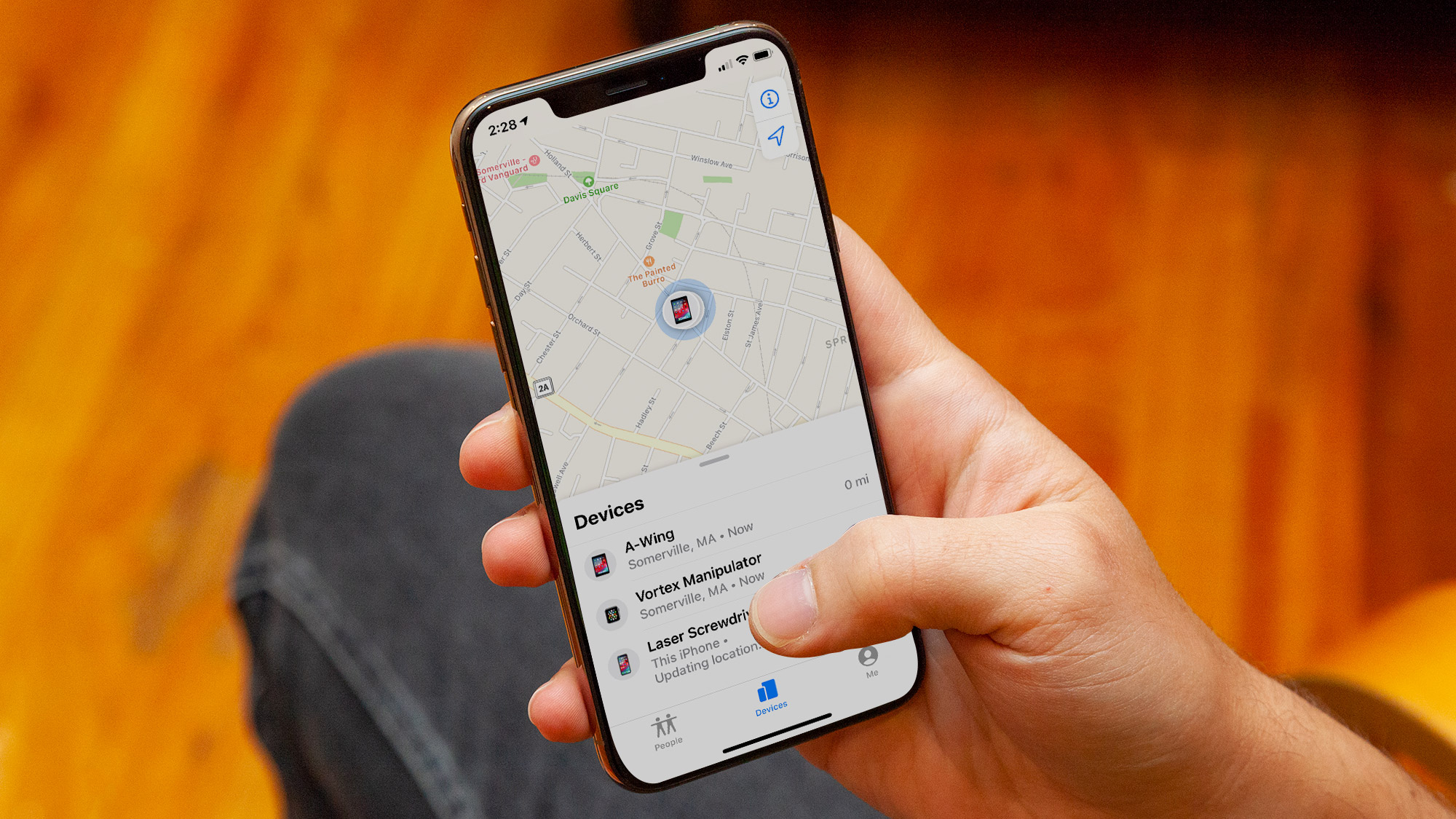
The hack effectively turns any Bluetooth enabled device into a fake AirTag
With the attack method we introduced, the attacker can achieve this.
What happens next?
That update was released on December 11 2024.

The hack effectively turns any Bluetooth enabled device into a fake AirTag
Apple also emphasized that the issue is not a vulnerability with Apple products.
It’s unclear whether this exploit has been utilized by bad actors right now.
They should also keep software up to date and consider privacy-focused operating systems for better protection against prying eyes.